IF YOU CAN’T SEE IT, YOU CAN’T MANAGE IT.
STEP OUT OF THE DARK.
COMPLETE COVERAGE OF THE CYBERSPACE
CyObs is a high-precision cyber radar system that offers a complete view of your country’s cyberspace, combining threat detection, risk management and insights needed to eliminate threats and reduce your attack surface.
Including dependencies and interfaces, reliable diagnostics, systematic analysis of cyberattacks and actionable recommendations.
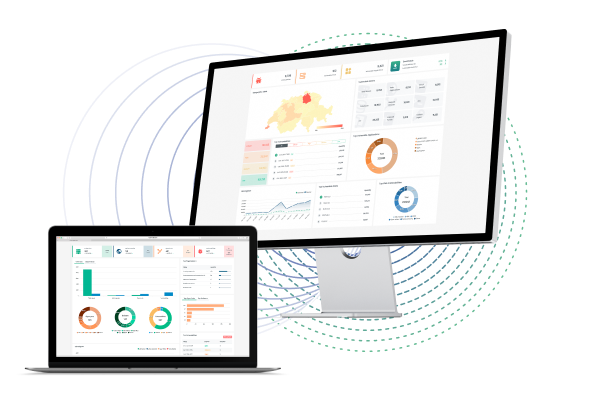
MAKING CYBERSPACE VISIBLE, MEASURABLE AND THUS, MANAGEABLE
A powerful tool for security-sensitive organisations that need to protect their critical assets and infrastructures
Comprehensive understanding of the cyber-environment through unprecedented visibility and insight.

Proactive identification and management of vulnerabilities in digital infrastructures.
Risk-based vulnerability prioritisation and remediation.

Identification of unusual activity and potential threats while avoiding alert fatigue and false positives.

Improvement of the overall security posture through real-time monitoring.
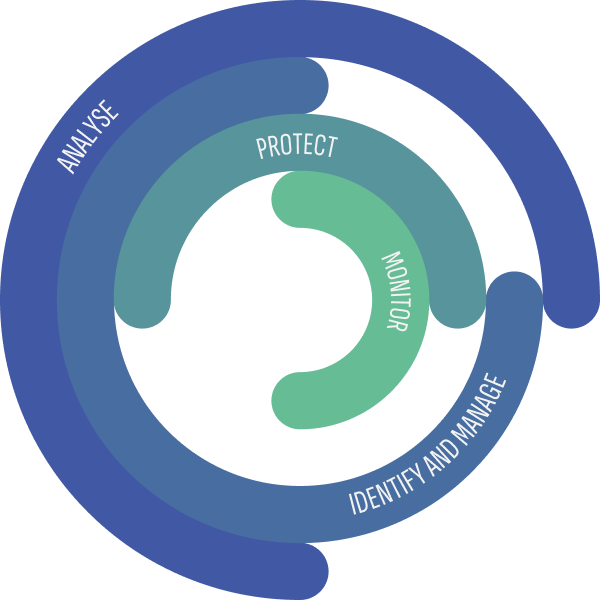
1. ANALYSE
- High-precision, high-speed analysis of digital infrastructure.
- Comprehensive understanding and visualisation of cyberspace.
- Advanced analytics capabilities for generating views of trends and historical data.
- Powerful exploration engine for navigating and analysing collected data.
2. IDENTIFY AND MANAGE
- Proactive identification of vulnerabilities.
- Anomaly detection capabilities to identify unusual activity and potential threats.
- Prioritisation tool for patching vulnerabilities based on their potential severity and impact.
3. PROTECT
- Reduction of the attack surface to improve overall security.
- Integration with existing security systems for a comprehensive defense.
- Detailed executive and technical reports with recommendations for vulnerability patching.
4. MONITOR
- Automated alerts and notifications to say ahead of potential threats and vulnerabilities.
- Regular updates and maintenance to ensure accurate results.
- Scalability to accommodate large and complex IT infrastructures.
Key Benefits
Strategic Insights:
Compliance:
helps organisations ensure regulatory compliance and avoid potential penalties through automated reporting capabilities.
Proactive Prevention:
offers a proactive and preventive approach to cybersecurity by anticipating potential security issues to minimise potential damages.
Risk Management:
helps to better identify, assess and manage potential risks through advanced analytics and anomaly detection capabilities.
Ease of Use:
provides an efficient, simple, easy to deploy and easy-to-use interface.
Cost-effectiveness:
reduces research, automates processes, eliminates false positives and customisable to meet specific organisational needs.
Flexibility:
engineered to accommodate the evolving needs of large and complex IT environments, offering support for on-premises, cloud, and hybrid solutions.
Data-driven decision-making:
provides actionable data and analytics that help monitor the performance of any unique security strategy.
Accuracy:
ensures accurate results and information security through regular updates and maintenance.
Scalability:
tailored to meet the varying demands of different size organisations.
See CyObs in Action
Schedule a demo to experience first-hand how CyObs helps minimise the attack surface and provides insights on critical assets.